What is the tangible thing that separates a red teamer from a criminal? Being told you are authorized is great, but it is intangible and may be inadmissible. The best proof of that authorization takes the form of a Letter of Authorization (LoA). The LoA is the single most essential tool for red teamers to carry during an operation. It is an excellent de-escalation tool and can keep you out of jail or other serious trouble. Having a valid, serious, and professional LoA that meets the below criteria has saved me when detained by security personnel, where a police helicopter was dispatched to search for me, and when police officers ran towards me with long guns pointed at my chest (more on that in a future post). There are many more benign instances of using LoAs as well, but they make for less exciting stories.
Your likelihood of using an LoA depends on your operation’s strategy and objectives. Broadly stated, there are two types of ends to red team operation:
Capture the Flag: You achieve specific objectives (e.g., stealing passwords from a safe or gaining persistent access to the network via a server room) and leave the premises, often without being detected.
You test security’s Deterrence, Prevention, and Detection capabilities. Response is only tested if detection capabilities are high (which is rare).
Escalate Until Caught: You achieve specific objectives and then continue to escalate the obviousness of your suspicious behavior until you are detected by security and/or other personnel and reported. This allows you to determine the detection threshold while documenting the strengths and weaknesses in security team’s response.
You test security’s Deterrence, Prevention, Detection, and Response capabilities.
From experience, I have used LoAs less than 10% of the time during Capture the Flag operations, and around 80% of the time during Escalate Until Caught assessments. I have carried an LoA on 100% of the tests I have conducted.
What is a Letter of Authorization?
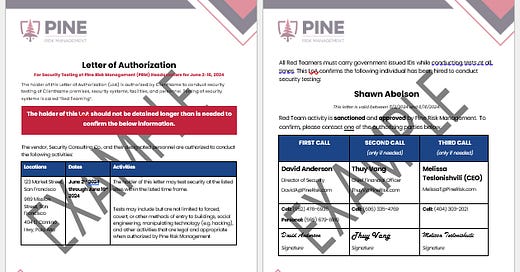
A LoA is (unsurprisingly) a letter that states you are authorized to be conducting the activities that you are conducting. All LoAs must be provided and signed by someone who has undisputed dominion to authorize you to conduct an assessment on the property. All effective LoAs generally have the same components and features:
Professionalism: During a high-stress situation, the LoA has to make a strong impression within seconds to a security officer, building manager, or law enforcement. LoAs should maintain a professional appearance.
Letterhead: LoAs should be on client letterhead.
Statement of Fact: A one or two sentence explanation of what the letter is. Something along the lines of “The holder of this letter is authorized by CLIENTNAME to conduct X activities.”
Detainment Statement: “The holder of this letter should not be detained any longer than it takes to substantiate the information listed within this letter.”
Name: The full legal first and last name of the red teamer.
Dates of Validity: The date range within which the letter is valid.
Location (Optional): The sites or locations for which the LoA is valid.
ID Check Statement (Encouraged): A statement that says the holder of the letter must be carrying government ID that matches the name on this letter.
Compliance Statement (Optional): For certain sites - that only allow individuals with hard hats or those who have complete certain types of training - the LoA may state that the red teamer has met all requirements for being at the site (assuming they actually have). This is to avoid situations where your red teaming activity is confirmed, but angry site personnel seek to use your lack of training completion, safety equipment, or other requirements against you or the security department.
First Call: The client points of contact who authorized the operation. This should include their full name, title, work phone number, and personal cell number (yes, really)
Note, you are asking these individuals to call a random phone number you provided to validate what would otherwise be criminal behavior. They are likely to be suspicious of the phone numbers you provide, and rightfully so. Encourage them to use internal messaging or work systems to call the individual. Bonus points if you include screenshots of these internal profiles on the LoA, or use internal language that provides an air of authenticity.
Second Call: A backup point of contact on the client team who is aware of the assessment. This is often the manager of the individual listed in the first call. This should include full name, title, and work and personal phone numbers.
Third Call: A backup to the backup that can get you out of trouble if your primary and secondary points of contact are not answering their phone. This has come in handy for me only once but when I needed it, I really needed it.
Optional Authentication
Option 1: Some organizations can publish internal posts, Wikis, or other announcements that the security team can view with a certain code. Once they enter the code or find a secret internal URL/page, they can view the names, photos, dates of engagement, and locations for the red team assessment. This provides quick and easy authentication on an internal system.
Option 2: For more advanced or mistrustful organizations, the LoAs can include bilateral authentication phrases. I rarely recommend this, but it can be helpful to ward off questions about fake LoAs or concerns regarding authenticity of the phone numbers. For option 2, follow these steps:
Print a unique authentication phrase on the LoA, something like “Charlie-Zulu-Delta-Xray.”
Print a counter-authentication letter and provide a sealed copy to the first call (GSOC, security director, or similar) which includes the same phrase.
If you present the LoA, the person you give the LoA to can ask the GSOC, director, or other individual who authorized the assessment for a specific authentication code. When they provide the right one, there is an additional sense that the letter is valid.
Additional note for Option 2: Ensure your escalation contacts are trained to this protocol and have complete understanding of what is expected of them.
Option 3: For organizations with frequent tests, there can be a phrase of the day/week/month that security officers are told during each shift brief. That phrase is to be used only by testers to prove their authenticity when caught.
Authorization Caveats
As red teamers, we would be remiss to not learn lessons from our peers. When two Coalfire red teamers were arrested and charged with felonies in Iowa in 2019, a turf war, contract debate, and scope of authority debate ensued between the local Sheriff’s office who were entrusted to secure the courthouse and the State Court Administration who oversaw the courthouse and its networks. The boundaries of authority for each party were blurry; however, the fact remains that Coalfire conducted tests of a law enforcement protected space without alerting or collaborating with law enforcement. Here are some key lessons learned:
Whoever signs the authorization letter must have the authority to authorize a penetration test.
If law enforcement protects a site, you should speak with their leadership and law enforcement leadership should be listed as the first or second calls on the bottom of the LoA.
If you are a consultant, check whether the entity hiring you is a building/landowner or tenant of a leased space. Ask them to review their lease to ensure it does not preclude the activity that you are intending to conduct. Understand the landlord (i.e. “base-building” security model, protocols, and policies.)
If you are part of a company, consider whether you own or lease a space. If you own it, you have significant latitude and greater authority over what occurs in your space. If you are a tenant of a space, review your agreement with the landlord, and ensure your red team tests only your security measures.
If you have a close relationship and/or rely on landlord security as part of your security model or layers of security, then you should work with your landlord and see if they are comfortable with their security being within the scope of the test. If that is the case, then a landlord leadership should be listed on the LoA as well.
Other Precautions
Two additional caveats come to mind in relation to Letters of Authorization:
Ensure the client points of contact listed in the LoA are available and will answer their phones during your test. If you plan a nighttime test, let them know ahead of time and ask them to keep a work or personal phone nearby that night. No matter when you test, it is a best practice to have a group chat (or multiple 1:1 threads) to inform them before activities start and when they end. This will ensure they are available and enable them to relax after the operations are complete.
Most red teamers keep their letters in their back pocket, or on the inside of a jacket or shirt. Many security officers are current or former law enforcement. When caught, a red teamer is typically doing something to significantly raise the concern and suspicion of security or law enforcement personnel. These facts combine to create a dangerous situation for the red teamer who may reach for their letter of authorization during the height of an escalated situation with security or law enforcement personnel. Red teamers must ask permission to reach for their LoA prior to reaching into the same place many people carry firearms. Red teamers should explain that they have a letter authorizing them to be there, that it is in their back pocket, and ask permission to show it to the officer.
Letters of Authorization ensure that red teamers are safe and successful in the course of their operations. They can effectively de-escalate situations and keep you out of trouble. Each of the above caveats and suggestions are based on more than a decade of conducting assessments, making mistakes, learning lessons, and improving my approach to ensure my teams are safe and secure.
Resources:
Letters of Authorization (LoA) are sensitive documents as they often provide trained security professionals with approval to do things that are otherwise considered crimes. Templates of LoAs are available to Locks & Leaks paid subscribers for professional use only. Those subscribers may click below to continue.